Terms & Conditions
Scope of Services
Details about the types of personal information collected, such as names, addresses, contact information, and possibly sensitive information related to interior services or projects.
Scope of Services
Details about the types of personal information collected, such as names, addresses, contact information, and possibly sensitive information related to interior services or projects.
Scope of Services
Details about the types of personal information collected, such as names, addresses, contact information, and possibly sensitive information related to interior services or projects.
Payment Terms
Measures taken to protect personal information from unauthorized access, disclosure, alteration, or destruction, which might include encryption, access controls, and regular security assessments.
Information about the methods used to securely dispose of or anonymize personal information once it is no longer needed for its original purpose. This might include shredding physical documents, deleting electronic records, or anonymizing data to remove identifying information.
Payment Terms
Measures taken to protect personal information from unauthorized access, disclosure, alteration, or destruction, which might include encryption, access controls, and regular security assessments.
Information about the methods used to securely dispose of or anonymize personal information once it is no longer needed for its original purpose. This might include shredding physical documents, deleting electronic records, or anonymizing data to remove identifying information.
Payment Terms
Measures taken to protect personal information from unauthorized access, disclosure, alteration, or destruction, which might include encryption, access controls, and regular security assessments.
Information about the methods used to securely dispose of or anonymize personal information once it is no longer needed for its original purpose. This might include shredding physical documents, deleting electronic records, or anonymizing data to remove identifying information.
Confidentiality
Measures taken to protect personal information from unauthorized access, disclosure, alteration, or destruction, which might include encryption, access controls, and regular security assessments.
Confidentiality
Measures taken to protect personal information from unauthorized access, disclosure, alteration, or destruction, which might include encryption, access controls, and regular security assessments.
Confidentiality
Measures taken to protect personal information from unauthorized access, disclosure, alteration, or destruction, which might include encryption, access controls, and regular security assessments.
Client Responsibilities
Explanation of how personal information is used to maintain the security of interior agency systems, prevent unauthorized access or fraud, and protect against other unlawful activities. Assurance that personal information will only be collected and used for purposes consistent with individuals' consent or preferences, where applicable, and in accordance with applicable privacy laws and regulations.
Client Responsibilities
Explanation of how personal information is used to maintain the security of interior agency systems, prevent unauthorized access or fraud, and protect against other unlawful activities. Assurance that personal information will only be collected and used for purposes consistent with individuals' consent or preferences, where applicable, and in accordance with applicable privacy laws and regulations.
Client Responsibilities
Explanation of how personal information is used to maintain the security of interior agency systems, prevent unauthorized access or fraud, and protect against other unlawful activities. Assurance that personal information will only be collected and used for purposes consistent with individuals' consent or preferences, where applicable, and in accordance with applicable privacy laws and regulations.
Termination of Services
Explanation of how personal information is used to maintain the security of interior agency systems, prevent unauthorized access or fraud, and protect against other unlawful activities. Assurance that personal information will only be collected and used for purposes consistent with individuals' consent or preferences, where applicable, and in accordance with applicable privacy laws and regulations.
Termination of Services
Explanation of how personal information is used to maintain the security of interior agency systems, prevent unauthorized access or fraud, and protect against other unlawful activities. Assurance that personal information will only be collected and used for purposes consistent with individuals' consent or preferences, where applicable, and in accordance with applicable privacy laws and regulations.
Termination of Services
Explanation of how personal information is used to maintain the security of interior agency systems, prevent unauthorized access or fraud, and protect against other unlawful activities. Assurance that personal information will only be collected and used for purposes consistent with individuals' consent or preferences, where applicable, and in accordance with applicable privacy laws and regulations.
Insurance and Liability
Explanation of how personal information is used to maintain the security of interior agency systems, prevent unauthorized access or fraud, and protect against other unlawful activities. Assurance that personal information will only be collected and used for purposes consistent with individuals' consent or preferences, where applicable, and in accordance with applicable privacy laws and regulations.
Insurance and Liability
Explanation of how personal information is used to maintain the security of interior agency systems, prevent unauthorized access or fraud, and protect against other unlawful activities. Assurance that personal information will only be collected and used for purposes consistent with individuals' consent or preferences, where applicable, and in accordance with applicable privacy laws and regulations.
Insurance and Liability
Explanation of how personal information is used to maintain the security of interior agency systems, prevent unauthorized access or fraud, and protect against other unlawful activities. Assurance that personal information will only be collected and used for purposes consistent with individuals' consent or preferences, where applicable, and in accordance with applicable privacy laws and regulations.
Project Timeline
Identification of the types of external entities with whom the agency may share personal information. This could include contractors, consultants, vendors, partner organizations, or other government agencies. Explanation of why the agency shares personal information with third parties. This might include facilitating services, conducting research or analysis, collaborating on projects, or complying with legal requirements.
Clarity on the specific categories of personal information shared with third parties and limitations on the purposes for which it may be used by those parties.
Project Timeline
Identification of the types of external entities with whom the agency may share personal information. This could include contractors, consultants, vendors, partner organizations, or other government agencies. Explanation of why the agency shares personal information with third parties. This might include facilitating services, conducting research or analysis, collaborating on projects, or complying with legal requirements.
Clarity on the specific categories of personal information shared with third parties and limitations on the purposes for which it may be used by those parties.
Project Timeline
Identification of the types of external entities with whom the agency may share personal information. This could include contractors, consultants, vendors, partner organizations, or other government agencies. Explanation of why the agency shares personal information with third parties. This might include facilitating services, conducting research or analysis, collaborating on projects, or complying with legal requirements.
Clarity on the specific categories of personal information shared with third parties and limitations on the purposes for which it may be used by those parties.
Change Orders
Details about the types of personal information collected, such as names, addresses, contact information, and possibly sensitive information related to interior services or projects.
Change Orders
Details about the types of personal information collected, such as names, addresses, contact information, and possibly sensitive information related to interior services or projects.
Change Orders
Details about the types of personal information collected, such as names, addresses, contact information, and possibly sensitive information related to interior services or projects.
Intellectual Property
Details about the types of personal information collected, such as names, addresses, contact information, and possibly sensitive information related to interior services or projects.
Intellectual Property
Details about the types of personal information collected, such as names, addresses, contact information, and possibly sensitive information related to interior services or projects.
Intellectual Property
Details about the types of personal information collected, such as names, addresses, contact information, and possibly sensitive information related to interior services or projects.
Frequent question
Frequent question
Frequent question
Got Questions? We've Got Answers
Got Questions?
We've Got Answers
Got Questions? We've Got Answers
the award-winning calendar app with powerful features including intuitive natural language text parsing.
the award-winning calendar app with powerful features including intuitive natural language text parsing.
the award-winning calendar app with powerful features including intuitive natural language text parsing.
What makes CalenTask different from other productivity apps?
CalenTask uniquely combines task management, event scheduling, and contact organization into one seamless experience. Our integrated calendar feature transforms your tasks and events into a dynamic to-do list, helping you manage your time more efficiently.
Can I integrate CalenTask with other apps I already use?
Is my data safe and secure on CalenTask?
Does CalenTask offer team collaboration features?
What makes CalenTask different from other productivity apps?
CalenTask uniquely combines task management, event scheduling, and contact organization into one seamless experience. Our integrated calendar feature transforms your tasks and events into a dynamic to-do list, helping you manage your time more efficiently.
Can I integrate CalenTask with other apps I already use?
Is my data safe and secure on CalenTask?
Does CalenTask offer team collaboration features?
What makes CalenTask different from other productivity apps?
CalenTask uniquely combines task management, event scheduling, and contact organization into one seamless experience. Our integrated calendar feature transforms your tasks and events into a dynamic to-do list, helping you manage your time more efficiently.
Can I integrate CalenTask with other apps I already use?
Is my data safe and secure on CalenTask?
Does CalenTask offer team collaboration features?
GEt started for free
Boost Your Productivity
Start Using Mubly Today!
The award-winning calendar app with powerful features including intuitive natural language text parsing.

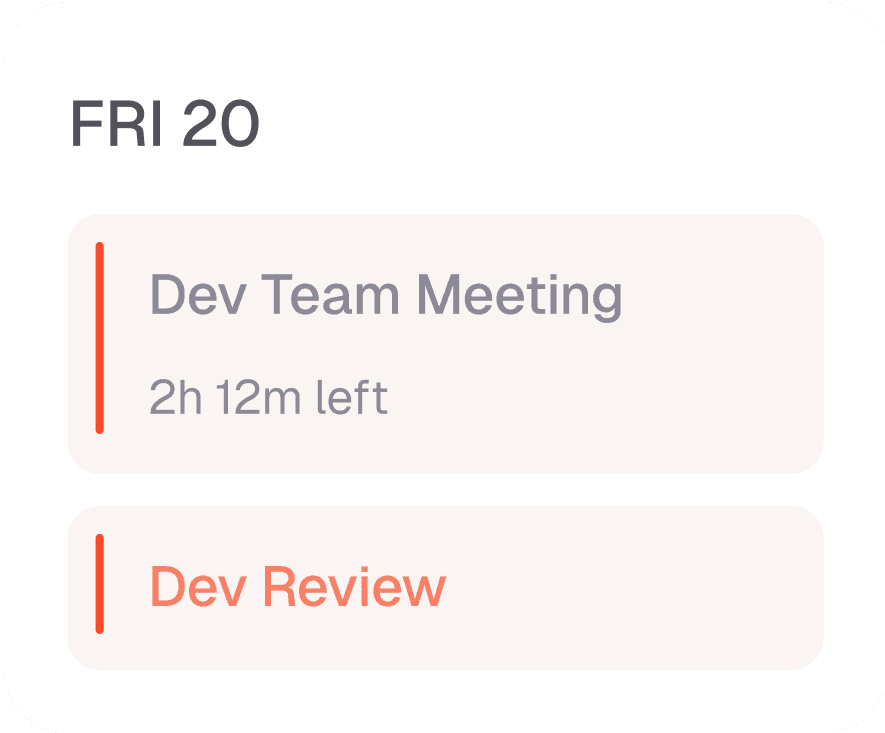
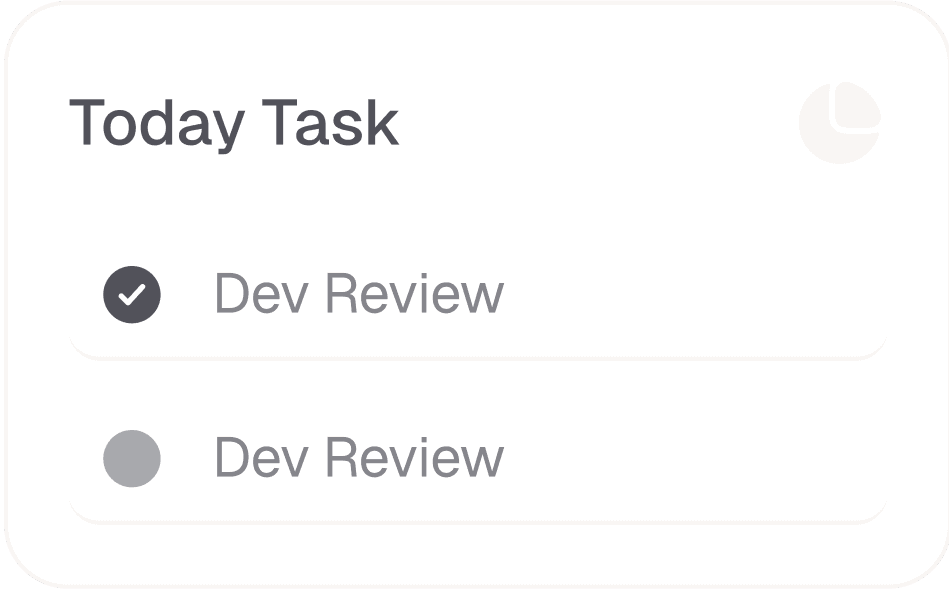
GEt started for free
Boost Your Productivity
Start Using Mubly Today!
The award-winning calendar app with powerful features including intuitive natural language text parsing.



GEt started for free
Boost Your Productivity
Start Using Mubly Today!
The award-winning calendar app with powerful features including intuitive natural language text parsing.


